Unmasking the Truth: Can Your VPN Really Keep You Anonymous Online?
I am a guy who cares about privacy. Like everyone, I spend much of my time online daily. But I connected to the VPN each time I began to surf online. As reading some deject story about someone who got into a miserable situation because of his identity being exposed. I begin to wonder if using a VPN could make you completely anonymous. I have spent countless time on this research, and the following words are what I want to share with you about all I have learned.
The VPN is not completely anonymous since there are many aspects of your online and real life that have your identity information, and they weave together with your activities in these areas. And the VPN only takes part in a tiny amount – some of your online everyday life.
In my humble opinion based on my experience of IT work for more than 30 years, it is almost impossible for an average person to be completely anonymous either on the internet or in real life, regardless of which technical tools you could take. Because staying anonymous is something that is against your own human nature. It would help if you had a superpower to be disciplined to try to implement it in your life, and there is no guarantee it will be successful. However, you still could achieve some anonymity on the internet by employing specific tools if you think that is crucial to prevent you from being harmed.
Why the VPN can’t provide you completely anonymous?
I’m not sure what you mean by anonymous. According to the dictionary of Cambridge, anonymous means made or done by someone whose name is not known or not made public. I think that perfectly describes what happens on the internet: someone notices something done by you but has no idea who you are, you won’t be identified!
That’s something we are pursuing on the internet or even in the real world. Before we talk about why a VPN can’t make you completely anonymous, let’s take a good look at the identifiers about you in real life and on the internet:
Identifiers in real life
- identity card
- Passport
- Driver License
- Postal Addresses
- Birth Certificate
- Social Security Card
- Landline Number
- Bank account
- Mobile Number
- Credit and debit cards
Internet identifiers
Any of the following information that has connections with your real-life identifiers mentioned above will identify you on the internet:
- email address
- IP address
- social media accounts
- online shopping accounts
The ways your adversaries use to get your personal data
Now we’ll dive into how your adversaries could collect your privacy, including your identifiers. And explore some places where we may mitigate. You can also refer to another article on this website to learn more about the private data your adversaries could collect online. There are three main ways, as listed below:
- Eavesdropping on your internet connection
- unauthorized access to your devices and network
- Collect your privacy information while you are access a website
Collect your privacy information while you are access a website
When you begin to surf the internet with your devices, no matter what the device is, a laptop, a smartphone, a tablet, etc. Without your acknowledgment, much data about your daily life and identity will be transmitted to another end you intend to reach, such as the website. For example, you may read some articles you are interested in here and watch a TV show with a streaming service or chat with your friends on a social media website.
Do you know what kinds of information about your daily life and identifiers have been exposed during these sessions? A lot, exceed your imagination:
- Your IP address: if the IP address is related to an account in your ISP that has the payment information, your adversaries can identify you with this information.
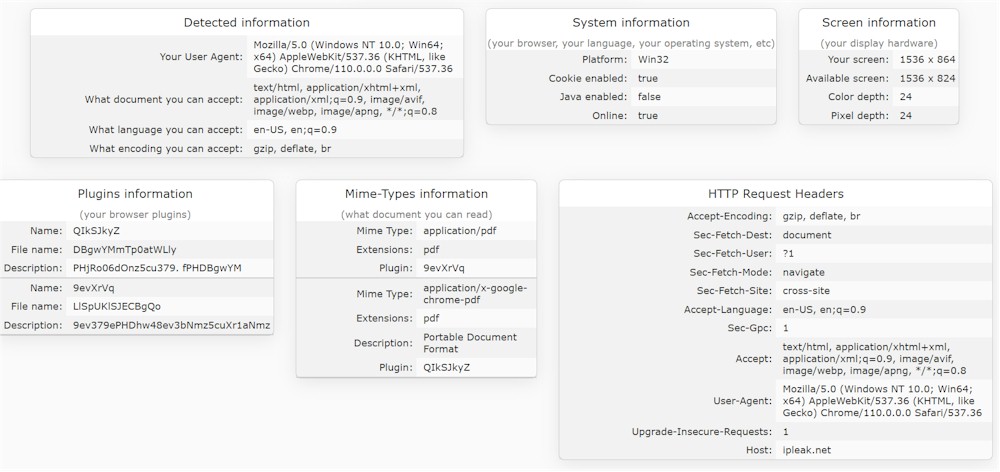
- Your digital fingerprint: information about your device, operation system, etc., is collected by the browser you use to surf the internet. All this information together will form your unique profile, and it’s extremely effective! Here I am going to share with you a screenshot of what this information looks like:
- Cookies: these yummy sounded staffs are containers all websites you access have placed in your computer or device. Information includes your login status, which pages you accessed and the time you spent on the pages, etc. These information containers stay in your device for a while and will be sent back to the masters who deployed them.
- Form data: Any information you type in the input box on a form, such as your email address, your login credentials, etc.
- The Referrer header: when you issue a request for a web page, the referrer header will be included in the request to show the server you intend to access where you come from. This information exposes which website you have accessed.
Eavesdropping on your internet connection
Now you acknowledge what information about your privacy will be gathered by another end while you are surfing online. And this information also can be intercepted by your adversaries while they are transmitted over the internet.
That will happen when you connect to a public Wifi Hotspot during a relaxing sunshine afternoon in a coffee bar. Or while you are waiting for your flight in an airport, sitting by the desk of a hotel room.
In that case, your adversaries will easily gather the information that tells a lot about you, like your interest, income, hobbies, the websites you have accessed, how many devices you have, and what type of them are, etc. Even worse, your identifiers may be grasped by your adversaries during the time. All the formations would be used for further attack if they thought it was necessary.
For example, your adversaries know that you prefer to read articles about how to losing weight, your mobile number or your social media account, etc. Based on it, they could conduct a phishing attack by sending you the link about losing weight to plant malicious software on your device. Then they could use any of their might to get control of your device. From the moment you were their meat.
Unauthorized access to your devices and network
Remember that all applications installed on your devices can access all data on your devices, including all your identifiers, when they have proper permissions.
Your adversaries or hackers have so many ways to get into your devices. The following are some very common:
- Phishing scams: Based on what they know about you, they would trick you into clicking the link that would download malicious software on your devices or provide sensitive information to them about your identifiers. For example, they may send you an email or chat on social media platforms that interest you to get their job done.
- Weak passwords: according to information about you that your adversaries collected, they could use dictionary or brute force attacks to crack your passwords when you use easily guessable passwords.
- Social engineering: using human psychology and the information about you that they already have from the previous attacks to trick you into giving up sensitive information to them or permitting them to access your devices.
- Download applications from unsafe places: Protent to be some applications you trust and know well to download them. What you don’t know is that the applications have been modified to have malicious codes that may download other malicious software stealthily.
- Physical access: your adversaries could steal your devices to get access to it directly or do it while you are not there.
As you can see above, your identifiers could be exposed to your adversaries in many ways from various resources, and among the information are what you have done on the internet, and the only place the VPN can be effective for making you anonymous is by preventing the data transmitted over the internet from being eavesdropped. Apart from that, almost all devices you use right now are spying on you. That is why the VPN can not make you completely anonymous online, and it’s far from that.
How to Test the Anonymity of Your VPN Connection
So, how can you test the anonymity of your VPN connection? Here are a few tests you can perform to ensure your VPN is providing the anonymity you expect:
- Connect to your VPN: Start by connecting to your VPN service, such as ExpressVPN. Make sure that you’re connected to a server location that is different from your physical location.
- Check your IP address: Once you’re connected, you can use a website like ipleak.net to check your IP address. This should match the location of the VPN server you’re connected to, not your physical location.
- Check the DNS leak test result: A DNS leak test is used to determine if your VPN connection is leaking DNS requests. This can occur if your VPN provider is not properly encrypting your DNS requests and they are being transmitted in plain text. You can scroll down a little to check whether there is any DNS query leak.
- Check for WebRTC leaks: WebRTC (Web Real-Time Communication) is a technology that enables real-time communication between browsers and mobile applications. It is commonly used for applications such as video chat, voice calling, and file sharing without requiring the use of plugins or additional software. WebRTC can also be used for other applications that require real-time, peer-to-peer communication, such as online gaming and live streaming. WebRTC can leak your real IP address, even when connected to a VPN. On the test result page on ipleak.net, you can see there is a section of Your IP addresses – WebRTC detection. If you saw the IP address of the ISP there, there are WebRTC leaks, or you are OK.
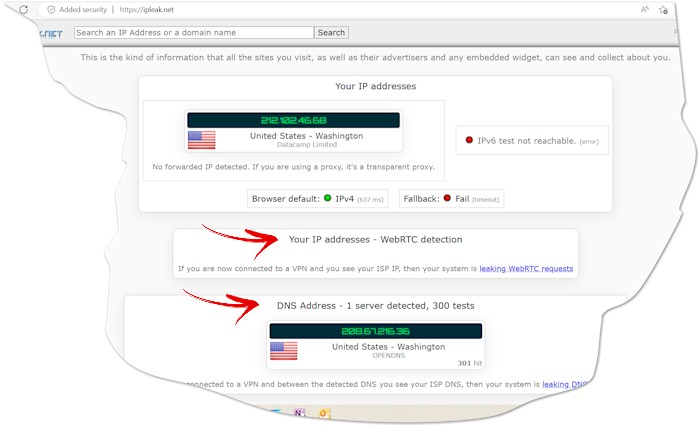
If your VPN passes all of these tests, then it’s providing you with the anonymity you expect. If it fails any of the tests, you may need to switch to a different VPN provider, or take steps to resolve the issue with your current provider.
How to ensure maximum anonymity with VPN
VPNs may be an excellent tool for improving online privacy and security, but they must be used correctly to maintain maximum anonymity. The kind of VPN protocol utilized, the encryption strength and the VPN provider’s logging rules are all factors that might impact the amount of anonymity given by a VPN. You may ensure optimal privacy while using a VPN by recognizing these issues and making educated decisions.
Choosing the right VPN protocol
The first step in ensuring maximum anonymity with a VPN is choosing the right VPN protocol. There are several VPN protocols available, including Lightway, OpenVPN, Wireguard, IkeV2, etc.Generally, you can choose the protocol from the setting of the VPN applications. Following are samples of currently the most popular VPN providers:
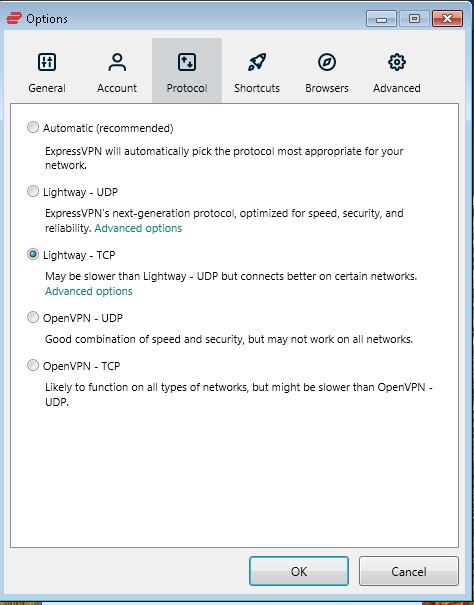
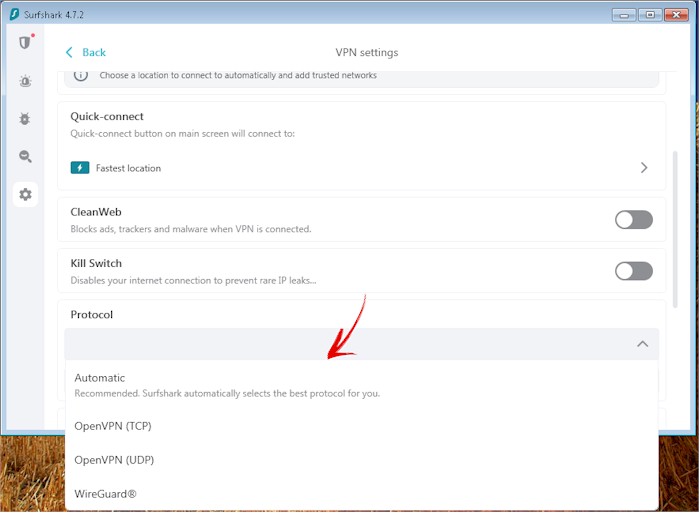
The OpenVPN protocol is generally considered to be the most secure VPN protocol available. It uses robust encryption algorithms and can be configured to use a variety of different encryption ciphers, including AES and Blowfish. Additionally, OpenVPN can operate over both TCP and UDP, allowing for greater flexibility and compatibility with different network configurations.
Lightway is a relatively new VPN protocol developed by ExpressVPN. While it’s not as widely used as other protocols like OpenVPN, WireGuard, and IPSec, Lightway has been designed to be lightweight, fast, and secure. It uses modern encryption algorithms like AES-256-GCM and ChaCha20-Poly1305 to encrypt the traffic and implements a zero-knowledge proof authentication mechanism. While it has not been widely audited or adopted yet, Lightway shows promise as a potentially secure and efficient VPN protocol.
WireGuard is a relatively new VPN protocol that has been designed to be fast, lightweight, and secure. It uses modern encryption algorithms like ChaCha20 and Poly1305, and is designed to minimize attack surface and avoid complex configurations. WireGuard is also easier to audit due to its minimalistic design.
IKEv2 uses strong encryption algorithms like AES and is designed to quickly establish and maintain secure VPN connections, even when network conditions are unstable, or the connection is interrupted. It also includes features like built-in NAT traversal and the ability to seamlessly switch between Wi-Fi and cellular networks. IKEv2 is a secure and efficient VPN protocol that is well-suited for use on mobile devices and in situations where a reliable and fast connection is important.
When I choose a VPN protocol to use, it’s no doubt that I always choose the one among all the VPN protocols mentioned above.
The encryption strength of a VPN
Another crucial thing to consider while guaranteeing optimal anonymity by using a VPN is the encryption quality. Strong encryption prevents your adversaries from intercepting your communication data and is crucial for ensuring privacy and security.
The encryption strength used in VPNs is determined by the encryption technique and key length employed. The strongest encryption algorithms used in VPNs are, in general, Advanced Encryption Standard (AES) with 256-bit keys and ChaCha20 with 256-bit keys. So that is why when I choose a VPN, I will make sure the VPN employs both.
No-Logs Policy
I have been using the VPN for more than thirteen years. In my opinion, the privacy or anonymity you could get from using a VPN depends on the trust you give to the VPN provider. Since all your communications go through the VPN server, the VPN provider has the absolute capability to gather all of them on their servers. If your VPN provider has gathered information about your identifiers and the activities on the internet, then hand it to your adversaries. You have no privacy or anonymity!
That is why, apart from choosing the right VPN protocol, and encryption strength, you have to make sure the VPN provider implements the no-logs policy in its practice. That means it does not gather any communications data of yours on the VPN server you connected to, and this on-logs policy practice has been audited by a reputed third party.
You can ensure the VPN provider you chose has implemented the no-logs policy by searching the related topic. For example, when I needed to find out whether Surfshark has a no-logs policy, I typed ‘no-logs policy, surfshark’ in the search box. Then I will get the information that I care:

There are various more actions that may be done to achieve optimum anonymity using a VPN, in addition to selecting the correct VPN protocol, encryption level, and logging policies. When subscribing to a VPN, for example, adopting an anonymous payment mechanism, such as Bitcoin, can assist preserve the privacy of customer payment information. Additionally, utilizing a secure browser with privacy-enhancing plugins, such as Tor or Firefox, can assist safeguard user privacy and security when accessing the internet.
How to be completely anonymous on the internet?
Though it is not impossible, to be completely anonymous on the internet, you need to employ OPSEC and Compartmentalization along with all technologies and tools you can use, including the VPN. The details of implementing strategies to be completely anonymous exceed the purpose of this post. Here I can provide you with some main points you can work on.
As I said at the beginning of this post, the key factor in whether you can stay anonymous or not is yourself, the human, who is always the weakest link of strategies to be anonymous.
Either OPSEC and Compartmentalization are both associated with yourself, the human. To successfully implement them to ensure complete anonymity on the internet, you need to be highly self-disciplined. Now let’s go ahead to learn what OPSEC and Compartmentalization are a bit.
Knowing what is OPSEC
OPSEC (Operations Security) is a process for identifying, controlling, and protecting sensitive information in order to prevent unauthorized disclosure, exploitation, or compromise. It’s used in both military and civilian contexts to protect sensitive information from being disclosed to unauthorized parties, and to maintain the confidentiality, integrity, and availability of critical information.
OPSEC involves several key steps:
- Identifying critical information: This involves determining what information is sensitive, critical, or valuable and needs to be protected. Certainly, they are your identifiers when we talk about the topic of anonymity.
- Analyzing the threats: This involves determining who might want to access or compromise the critical information and how they might do so. We have discussed this above.
- Implementing countermeasures: This involves implementing security measures and controls to prevent unauthorized disclosure, exploitation, or compromise of the critical information.
- Monitoring and reviewing: This involves regularly monitoring the security posture and reviewing the security measures to ensure they remain effective and up-to-date.
OPSEC is important for protecting sensitive information in a variety of contexts, including military operations, government agencies, critical infrastructure, and business organizations. By following the OPSEC process, organizations can help ensure the confidentiality, integrity, and availability of their critical information, and reduce the risk of data breaches, cyber attacks, or other security incidents.
Understand what is compartmentalization
Compartmentalization refers to the practice of separating different aspects of a user’s online activity into separate, isolated spaces, or “compartments.” The aim of compartmentalization is to prevent data or activities in one area from affecting or being affected by data or activities in another area, thereby reducing the risk of data breaches, cyber attacks, or unwanted cross-contamination.
Here is how I implemented the compartmentalization in my digital life:
- Using (VPNs): use a VPN to create an encrypted, isolated network connection between a device and the internet, compartmentalizing the my internet activity from the rest of the network.
- Using Virtual machines: Virtual machines can be used to create isolated, virtual environments for running different types of software or performing different types of online activities. I use Whonix to create the VM. Whonix is particularly useful for those who are concerned about privacy and security and want to reduce their digital footprint, as well as for those who need to access the internet in an environment that is protected from prying eyes.
- Compartmentalize each online persona from the others: I have created as many Whonix VMs as I need. Each one has its own persona, such as a unique email address, a bitcoin wallet, and a virtual address. I keep doing only specific things on the one Whonix VM. That way, if one persona gets into trouble, others will not be affected.
Actually, it is very easy to cause the information to be connected to each other. If that happens, you will lose your online anonymity. So it all depends on whether or not you can act according to OPSEC strictly.
Mix your bitcoin
Since bitcoin was designed not to make you anonymous, all transactions you have made will be booked in the back chain. They are open to the public and can be tracked. This means that the history of each bitcoin can be easily traced from its original owner to its current owner. In order to stay anonymous, another important job you need to have done is to mix your bitcoin.
Mix bitcoin, also known as bitcoin tumbling or bitcoin laundering, is proceeded by breaking the connection between the original owner of the bitcoins and their current owner. It has been done by pooling bitcoins from multiple users, shuffling the coins to create a confusing trail, and then distributing the mixed coins back to the users in a way that makes it difficult to trace the origin of each coin.
Some popular Bitcoin mixing services include CoinJoin, BitMixer, and Helix by Grams. You can search to get more information about how to choose and use them to fit your need.
Okay, I have shared with you some main points that you can build as the foundation of being completely anonymous on the internet. From there, you can work on pursuing your objective of the thing that really matters to you, freedom.