How to defend yourself from malicious codes in seemingly legitimate Word or PDF documents
A few months ago, I received an email from a friend with an attachment that looked like a Word document. It had a catchy title and I was curious to see what it was. I opened the attachment and nothing happened. Or so I thought. The next day, I noticed that my computer was acting weird. It was slow, it showed pop-ups, it crashed randomly. I realized that something was wrong and I scanned my computer with an antivirus software. To my horror, I found out that the attachment had a hidden code that infected my computer with a virus. Luckily, I was able to remove the virus and fix my computer, but it took me a lot of time and effort. I learned a valuable lesson that day: never open attachments from unknown sources or without checking them first. And that’s what I want to share with you in this blog post: how to check and protect your documents from malicious codes.
Malicious codes are programs or scripts that can harm a computer system or its data. They can be hidden in Word or PDF documents and executed when the user opens them. To defend oneself from malicious codes, one should scan the documents with an antivirus software, verify the sender and the source of the documents, and avoid opening suspicious or unsolicited attachments.
You might think that scanning and verifying your documents is enough to keep you safe from malicious codes, but there is more to it than that. There are different types of malicious codes, such as viruses, worms, trojans, ransomware, spyware, and more. Each one of them can cause different kinds of damage to your computer or your data. You need to know how to recognize them, how to prevent them, and how to remove them if you ever get infected. That’s why I have prepared a complete guide for you on how to defend yourself from malicious codes in seemingly legitimate Word or PDF documents. In this guide, you will learn everything you need to know about this topic, from the basics to the advanced tips and tricks. You will also find some examples and screenshots to help you understand better. This guide is easy to follow and suitable for anyone who uses Word or PDF documents regularly. Don’t miss this opportunity to learn how to protect yourself and your computer from malicious codes. Keep reading and discover how to stay safe online!
What are malicious codes and how do they work?
Malicious codes are programs or scripts that can harm a computer system or its data. They can be hidden in Word or PDF documents and executed when the user opens them. Malicious codes can cause damage, steal data, or gain unauthorized access to systems. Malicious codes can be spread by visiting infected websites or clicking on bad email links or attachments.
There are different types of malicious codes, such as viruses, worms, trojans, ransomware, spyware, and more. Each one of them can cause different kinds of damage to your computer or your data. Here are some examples of malicious codes and how they work:
- Viruses are programs that attach themselves to other files or programs and infect them when they are run. They can delete, modify, or corrupt files, slow down the system, display unwanted messages, or create backdoors for hackers.
- Worms are programs that self-replicate and spread across computers in a network. They can consume bandwidth, overload servers, delete files, or install other malicious codes.
- Trojans are programs that disguise themselves as legitimate software or files but contain malicious code. They can open backdoors for hackers, steal information, spy on user activity, or download other malicious codes.
- Ransomware are programs that encrypt the user’s files or lock the system and demand a ransom for decryption or unlocking. They can prevent the user from accessing their data, extort money, or expose sensitive information.
- Spyware are programs that monitor the user’s activity, keystrokes, browsing history, or personal information. They can steal passwords, credit card numbers, identity information, or send spam emails.
Malicious codes can be written intentionally by hackers, disgruntled employees, competitors, or cybercriminals for various motives such as financial gain, revenge, challenge, or terrorism. They can also be injected accidentally by users who download pirated software, open phishing emails, or visit malicious websites.
Malicious codes can be hard to detect and remove because they often use encryption, obfuscation, anti-debugging techniques, or rootkits to hide themselves from antivirus software or system scans. They can also change their behavior or appearance to avoid signature-based detection. Therefore, it is important to use multiple layers of protection and prevention measures to defend yourself from malicious codes. In the next sections, we will discuss how to scan and verify your Word or PDF documents before opening them, how to identify the type and the source of the malicious code in your document, how to prevent and remove different types of malicious codes from your computer, how to recover your data and restore your system after a malicious code attack, and how to avoid common mistakes and pitfalls when dealing with malicious codes. Stay tuned!
How to scan and verify your Word or PDF documents before opening them?
One of the best ways to prevent malicious codes from infecting your computer is to scan and verify your Word or PDF documents before opening them. This can help you detect any hidden scripts, exploits, or objects that might harm your system or data. There are different tools and techniques that you can use to scan and verify your documents, depending on the file type and the level of analysis you need. Here are some of them:
- Antivirus software: This is the most basic and essential tool that you should have on your computer. Antivirus software can scan your files for known signatures of malicious codes and alert you if they find any. You should always keep your antivirus software updated and run regular scans on your system. You should also scan any new files that you download or receive before opening them. Some antivirus software can also scan email attachments or web downloads automatically.
- Online scanners: If you don’t have antivirus software or you want a second opinion, you can use online scanners to upload and scan your files for malicious codes. There are many online scanners available, such as VirusTotal, Hybrid Analysis, or MetaDefender. These scanners can use multiple antivirus engines and malware analysis tools to check your files for any suspicious behavior or indicators.
- PDF analyzers: If you want to analyze PDF files in more depth, you can use specialized tools that can examine the structure, content, and JavaScript of PDF files. These tools can help you identify any obfuscated or malicious code that might exploit PDF vulnerabilities or execute unwanted actions. Some examples of PDF analyzers are PDF Examiner, PDFiD, or Peepdf .
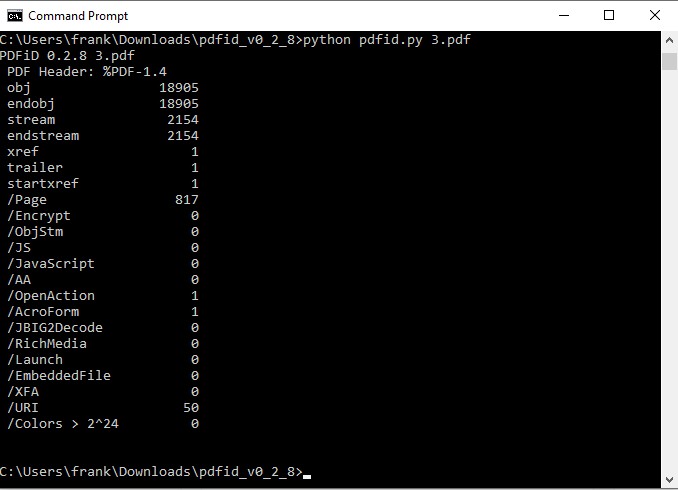
- Office analyzers: If you want to analyze Word or other Office files in more depth, you can use specialized tools that can extract and analyze the macros, embedded objects, or ActiveX controls of Office files. These tools can help you identify any malicious code that might exploit Office vulnerabilities or execute unwanted actions. Some examples of Office analyzers are Olevba, Oledump, or OfficeMalScanner.
To illustrate how to scan and verify your documents using some of these tools, let’s look at an example of a malicious PDF file that contains an exploit for CVE-2008-2992, a vulnerability in Adobe Reader that allows remote code execution. Suppose you receive this file as an email attachment from an unknown sender. How can you check if it is safe to open?
- First, you can use an online scanner like VirusTotal to upload and scan the file. VirusTotal will show you the results from multiple antivirus engines and tell you if the file is detected as malicious or not. In this case, VirusTotal shows that 29 out of 59 engines detected the file as malicious.
- Second, you can use a PDF analyzer like PDF Examiner to upload and analyze the file. PDF Examiner will show you the structure, content, and JavaScript of the PDF file and tell you if it contains any exploits or suspicious code. In this case, PDF Examiner shows that the file contains an exploit for CVE-2008-2992.
- Third, you can use a hex editor like HxD to open and view the file in hexadecimal format. A hex editor can help you see the raw data of the file and look for any hidden or obfuscated code. In this case, HxD shows that the file contains a shellcode that is XOR-encoded with a key of 0x36.
By using these tools and techniques, you can confirm that the file is indeed malicious and avoid opening it on your computer. You can also report it to your email provider or security team and delete it from your system.
As you can see, scanning and verifying your Word or PDF documents before opening them is a good practice that can help you defend yourself from malicious codes. However, scanning and verifying alone is not enough. You also need to know how to identify the type and the source of the malicious code in your document, how to prevent and remove different types of malicious codes from your computer, how to recover your data and restore your system after a malicious code attack, and how to avoid common mistakes and pitfalls when dealing with malicious codes. In the next sections, we will cover these topics in more detail. Don’t miss them!
How to identify the type and the source of the malicious code in your document?
After scanning and verifying your Word or PDF documents, you might find out that they contain some malicious code that could harm your computer or data. But how can you tell what kind of malicious code it is and where it came from? Identifying the type and the source of the malicious code can help you understand the threat level, the attack vector, and the mitigation strategy. There are different tools and techniques that you can use to identify the type and the source of the malicious code in your document, depending on the file type and the level of analysis you need. Here are some of them:
- Online scanners: As mentioned before, online scanners like VirusTotal, Hybrid Analysis, or MetaDefender can scan your files for malicious codes and tell you if they are detected by multiple antivirus engines and malware analysis tools. They can also provide you with some information about the type and the source of the malicious code, such as the name, the family, the behavior, the indicators of compromise (IOCs), or the origin. For example, VirusTotal can show you a summary of the detection results, including the name of the malicious code, its family or variant, its tags or categories, its relations to other files or URLs, or its community score.
- PDF analyzers: As mentioned before, PDF analyzers like PDF Examiner, PDFiD, or Peepdf can examine the structure, content, and JavaScript of PDF files and tell you if they contain any exploits or suspicious code. They can also provide you with some information about the type and the source of the malicious code, such as the exploit name, the CVE number, the shellcode, or the payload. For example, PDF Examiner can show you a detailed report of the analysis results, including the exploit name, its CVE number, its description, its references, or its mitigation.
- Office analyzers: As mentioned before, Office analyzers like Olevba, Oledump, or OfficeMalScanner can extract and analyze the macros, embedded objects, or ActiveX controls of Office files and tell you if they contain any malicious code. They can also provide you with some information about the type and the source of the malicious code, such as the macro name, its VBA code, its obfuscation techniques, its IOCs, or its payload. For example, Olevba can show you a summary of the analysis results, including the macro name, its VBA code snippet, its suspicious keywords or IOCs.
- Hex editors: As mentioned before, hex editors like HxD can open and view files in hexadecimal format. A hex editor can help you see the raw data of files and look for any hidden or obfuscated code. You can also use a hex editor to decode or decrypt any encoded or encrypted code using various methods such as XORing. For example, HxD can show you a dialog box where you can enter a key to XOR a selected portion of data.
By using these tools and techniques, you can identify the type and the source of the malicious code in your document. You can also compare your findings with other sources such as online databases (e.g., CVE), threat intelligence platforms (e.g., MITRE ATT&CK), security blogs (e.g., Snyk), or security forums (e.g., Stack Exchange) to get more insights about the malicious code. However, identifying alone is not enough. You also need to know how to prevent and remove different types of malicious codes from your computer, how to recover your data and restore your system after a malicious code attack, and how to avoid common mistakes and pitfalls when dealing with malicious codes. In the next sections, we will cover these topics in more detail. Stay tuned!
How to prevent and remove different types of malicious codes from your computer?
Even if you scan and verify your Word or PDF documents before opening them, you might still encounter some malicious codes that manage to bypass your security measures and infect your computer. In that case, you need to know how to prevent and remove different types of malicious codes from your computer. Preventing and removing malicious codes can help you avoid further damage, data loss, or unauthorized access. There are different tools and techniques that you can use to prevent and remove malicious codes from your computer, depending on the type and the severity of the infection. Here are some of them:
- Antivirus software: As mentioned before, antivirus software is the most basic and essential tool that you should have on your computer. Antivirus software can not only scan your files for malicious codes, but also prevent them from running or spreading on your system. Antivirus software can also remove malicious codes from your infected files or quarantine them for further analysis. You should always keep your antivirus software updated and run regular scans on your system. You should also use a reputable antivirus software from a trusted vendor.
- Anti-malware software: In addition to antivirus software, you might also need anti-malware software to deal with some types of malicious codes that antivirus software might not be able to detect or remove. Anti-malware software can specialize in certain types of malicious codes, such as ransomware, spyware, rootkits, or adware. Anti-malware software can also provide additional features, such as firewall, browser protection, password manager, or VPN. You should use anti-malware software that is compatible with your antivirus software and avoid using multiple anti-malware software at the same time.
- System restore: If your computer is infected by a malicious code that causes system instability or corruption, you might need to use system restore to revert your system to a previous state before the infection occurred. System restore is a feature in Windows that allows you to create restore points that contain the configuration settings and critical system files of your system at a certain point in time. You can use system restore to undo changes made by malicious codes or other problems without affecting your personal files. You should enable system restore on your computer and create restore points regularly or before making any major changes to your system.
- Safe mode: If your computer is infected by a malicious code that prevents you from accessing your system normally or running security software, you might need to use safe mode to troubleshoot and fix the problem. Safe mode is a diagnostic mode in Windows that starts your system with only the essential drivers and services needed to run Windows. Safe mode can help you isolate the problem, disable or remove the malicious code, or perform other recovery actions. You can access safe mode by pressing F8 or Shift+F8 during the boot process or by using advanced startup options in Windows settings.
- Backup and recovery: If your computer is infected by a malicious code that encrypts or deletes your files, such as ransomware, you might need to use backup and recovery to restore your files from a backup copy. Backup and recovery is a process of creating and storing copies of your files on another device or location, such as an external hard drive or a cloud service. Backup and recovery can help you recover your files in case of data loss due to malicious codes or other disasters. You should backup your files regularly and keep multiple copies of them in different locations.
To illustrate how to prevent and remove different types of malicious codes from your computer using some of these tools and techniques, let’s look at an example of a ransomware infection that encrypts your files and demands payment for decryption. Suppose you receive an email from an unknown sender with an attachment that looks like a Word document. You open the attachment without scanning it first and see a message that says:
Your files have been encrypted by a ransomware called CryptoLocker. You are asked to pay a certain amount of money in Bitcoin within 72 hours or else your files will be deleted permanently. What can you do?
- First, you should disconnect your computer from the internet and any other devices or networks to prevent the ransomware from spreading further. You should also avoid paying the ransom or contacting the attackers, as there is no guarantee that they will decrypt your files or not infect them again.
- Second, you should use antivirus software or anti-malware software to scan your computer for the ransomware and try to remove it. You might need to use safe mode to access your system or run security software. You should also check your system for any other malicious codes or vulnerabilities that might have allowed the ransomware to infect your computer.
- Third, you should use backup and recovery to restore your files from a backup copy. You might need to use another device or location to access your backup copy. You should also verify that your backup copy is not infected by the ransomware or any other malicious codes. If you don’t have a backup copy, you might try to use some data recovery tools or services, but they might not work or be very expensive.
- Fourth, you should use system restore to revert your system to a previous state before the infection occurred. You might need to use safe mode or advanced startup options to access system restore. You should also check your system for any changes made by the ransomware or any other malicious codes.
- Fifth, you should update your system and security software and enable system restore and backup and recovery on your computer. You should also follow some best practices to prevent future ransomware infections, such as scanning and verifying your files before opening them, avoiding suspicious links and attachments, using strong passwords and encryption, and educating yourself and others about ransomware and other malicious codes.
By using these tools and techniques, you can prevent and remove different types of malicious codes from your computer. However, preventing and removing alone is not enough. You also need to know how to recover your data and restore your system after a malicious code attack, and how to avoid common mistakes and pitfalls when dealing with malicious codes. In the next sections, we will cover these topics in more detail. Stay tuned!
How to recover your data and restore your system after a malicious code attack?
Even if you prevent and remove different types of malicious codes from your computer, you might still suffer some data loss or system damage as a result of the attack. In that case, you need to know how to recover your data and restore your system after a malicious code attack. Recovering your data and restoring your system can help you resume your normal operations and minimize the impact of the attack. There are different tools and techniques that you can use to recover your data and restore your system after a malicious code attack, depending on the type and the severity of the infection. Here are some of them:
- Backup and recovery: As mentioned before, backup and recovery is a process of creating and storing copies of your files on another device or location, such as an external hard drive or a cloud service. Backup and recovery can help you recover your files in case of data loss due to malicious codes or other disasters. You should backup your files regularly and keep multiple copies of them in different locations. You should also verify that your backup copies are not infected by malicious codes or any other problems. To recover your files from a backup copy, you can use various tools or methods, such as Windows File History, Windows Backup and Restore, or third-party backup software.
- Data recovery software: If you don’t have a backup copy of your files or if your backup copy is also infected by malicious codes, you might need to use data recovery software to try to recover your files from your hard disk or other storage devices. Data recovery software can scan your storage devices for deleted or corrupted files and attempt to restore them to their original state. However, data recovery software might not work or be very expensive, depending on the type and the extent of the damage caused by the malicious codes. Some examples of data recovery software are Recuva, EaseUS Data Recovery Wizard, or Stellar Data Recovery.
- System restore: As mentioned before, system restore is a feature in Windows that allows you to create restore points that contain the configuration settings and critical system files of your system at a certain point in time. System restore can help you undo changes made by malicious codes or other problems without affecting your personal files. You should enable system restore on your computer and create restore points regularly or before making any major changes to your system. To restore your system to a previous state using system restore, you can use various tools or methods, such as Windows Recovery Environment, Control Panel, or Advanced Startup Options.
- System image: A system image is a complete copy of your entire system, including all the files, programs, settings, and drivers. A system image can help you restore your system to its exact state at the time the image was created. You can create a system image using various tools or methods, such as Windows Backup and Restore, Windows Recovery Environment, or third-party backup software. You should create a system image regularly or before making any major changes to your system. You should also store the system image on another device or location that is not affected by the malicious codes. To restore your system from a system image, you can use various tools or methods, such as Windows Recovery Environment, Control Panel, or Advanced Startup Options.
- System reset: A system reset is an option in Windows that allows you to reinstall Windows without affecting your personal files. A system reset can help you fix any problems caused by malicious codes or other issues that affect the performance or stability of your system. However, a system reset will remove any apps that you installed from sources other than Microsoft Store. You should backup your apps and settings before performing a system reset. To perform a system reset, you can use various tools or methods, such as Windows Settings, Control Panel, or Advanced Startup Options.
To illustrate how to recover your data and restore your system after a malicious code attack using some of these tools and techniques, let’s look at an example of a spyware infection that monitors your activity, keystrokes, browsing history, or personal information. Suppose you download a free software from an untrusted website without scanning it first and install it on your computer. The software contains spyware that steals your passwords, credit card numbers, identity information, or sends spam emails. What can you do?
- First, you should disconnect your computer from the internet and any other devices or networks to prevent the spyware from sending any more information to its server or downloading any more malicious codes on your system.
- Second, you should use antivirus software or anti-malware software to scan your computer for the spyware and try to remove it. You might need to use safe mode to access your system or run security software. You should also check your system for any other malicious codes or vulnerabilities that might have allowed the spyware to infect your computer.
- Third, you should use backup and recovery to restore your files from a backup copy. You might need to use another device or location to access your backup copy. You should also verify that your backup copy is not infected by the spyware or any other malicious codes. If you don’t have a backup copy, you might try to use some data recovery software or services, but they might not work or be very expensive.
- Fourth, you should use system restore or system image to restore your system to a previous state before the infection occurred. You might need to use safe mode or advanced startup options to access system restore or system image. You should also check your system for any changes made by the spyware or any other malicious codes.
- Fifth, you should update your system and security software and enable system restore, backup and recovery, and system image on your computer. You should also follow some best practices to prevent future spyware infections, such as scanning and verifying your files before opening them, avoiding suspicious links and attachments, using strong passwords and encryption, and educating yourself and others about spyware and other malicious codes.
By using these tools and techniques, you can recover your data and restore your system after a malicious code attack. However, recovering and restoring alone is not enough. You also need to know how to avoid common mistakes and pitfalls when dealing with malicious codes. In the next section, we will cover this topic in more detail. Stay tuned!
How to avoid common mistakes and pitfalls when dealing with malicious codes?
Dealing with malicious codes can be a challenging and complex task that requires technical skills, experience, and best practices. However, even the most skilled and experienced professionals can make some common mistakes and pitfalls when dealing with malicious codes. These mistakes and pitfalls can result in further damage, data loss, or security breaches. Therefore, it is important to avoid them and learn from them. Here are some of the common mistakes and pitfalls when dealing with malicious codes and how to avoid them:
- Paying the ransom: When faced with a ransomware attack that encrypts or locks your files or system and demands payment for decryption or unlocking, you might be tempted to pay the ransom to get your data back quickly and easily. However, this is a mistake that you should avoid for several reasons. First, paying the ransom does not guarantee that you will get your data back or that it will not be infected again. Second, paying the ransom encourages the attackers to continue their malicious activities and target more victims. Third, paying the ransom might expose your financial information or identity to the attackers or other criminals. Instead of paying the ransom, you should try to remove the ransomware from your system using security software or tools, restore your data from a backup copy or using data recovery software or services, report the attack to law enforcement, and follow some best practices to prevent future ransomware infections.
- Opening suspicious links or attachments: One of the most common ways that malicious codes infect your system is through phishing emails that trick you into clicking on a link or opening an attachment that contains malicious code. These emails can appear to come from legitimate sources, such as your bank, your employer, or your friends. However, they are designed to exploit your curiosity, fear, or greed and make you take an action that compromises your security. Instead of opening suspicious links or attachments, you should verify the sender and the source of the email, check the spelling and grammar of the email, hover over the link or attachment to see its actual destination or name, scan the link or attachment with security software before opening it, and delete any email that looks suspicious or unsolicited.
- Using weak passwords or encryption: Another common way that malicious codes infect your system is through brute-force attacks that try to guess your passwords or encryption keys by using automated tools or dictionaries. These attacks can succeed if you use weak passwords or encryption that are easy to guess or crack. Weak passwords or encryption can also expose your data to unauthorized access or theft by attackers who intercept your network traffic or access your storage devices. Instead of using weak passwords or encryption, you should use strong passwords or encryption that are hard to guess or crack. Strong passwords or encryption should be long, complex, unique, and random. You should also use different passwords or encryption for different accounts or devices, change them regularly, store them securely using password managers or encryption software, and avoid sharing them with anyone.
- Disabling security software or updates: Sometimes, you might disable your security software or updates for various reasons, such as improving performance, saving bandwidth, testing new features, or troubleshooting problems. However, this is a mistake that you should avoid because it leaves your system vulnerable to malicious codes that can exploit any known or unknown vulnerabilities in your system. Instead of disabling security software or updates, you should always keep them enabled and updated on your system. Security software and updates can protect your system from malicious codes by scanning your files for known signatures of malicious codes, preventing them from running or spreading on your system, removing them from your infected files or quarantining them for further analysis, patching any vulnerabilities in your system that could be exploited by malicious codes, and alerting you of any suspicious activity on your system.
- Ignoring backup and recovery: Sometimes, you might ignore backup and recovery for various reasons, such as lack of time, resources, knowledge, or interest. However, this is a mistake that you should avoid because it puts your data at risk of loss due to malicious codes or other disasters. Instead of ignoring backup and recovery, you should always perform backup and recovery on your system. Backup and recovery can help you recover your data in case of data loss due to malicious codes or other disasters. You should backup your data regularly and keep multiple copies of them in different locations. You should also verify that your backup copies are not infected by malicious codes or any other problems. You should also use various tools or methods to restore your data from a backup copy in case of data loss.
By avoiding these common mistakes and pitfalls when dealing with malicious codes, you can improve your security and reduce your risks. However, avoiding alone is not enough. You also need to follow some best practices and guidelines when dealing with malicious codes. In the previous sections, we have covered some of these best practices and guidelines, such as scanning and verifying your files before opening them, using strong passwords and encryption, updating your system and security software, and enabling system restore and backup and recovery on your computer. You should also educate yourself and others about malicious codes and their types, sources, impacts, and mitigation strategies. By following these best practices and guidelines, you can prevent, detect, remove, recover, and avoid malicious codes effectively and efficiently.