Can Someone Tell If You Are Using a VPN
I’ve always been keen on digital privacy and security, not just for myself, but for helping others navigate the complex online world. I remember it clearly. It was a quiet Saturday evening, rain drumming softly against my office window as I sat alone, a mug of lukewarm coffee beside my trusty Android tablet. That night, I was simply trying to access some region-locked content, something I knew a good VPN should handle. Despite using a reputable VPN service with its strong encryption and verified no-logs policy, I kept hitting that frustrating “proxy or unblocker” message. It wasn’t just Netflix; I’ve noticed how increasingly aggressive many services have become in their VPN blocking efforts. As a cybersecurity architect, this piqued my professional curiosity: how were they detecting my VPN so consistently, even when I was trying different servers or clearing my browser’s cache and cookies?
What I have learned confirm that Internet Service Providers (ISPs) and websites employ a range of sophisticated techniques, from identifying known VPN server IP addresses and specific VPN protocols through associated ports like OpenVPN’s 1194 or WireGuard’s 51820, to more advanced deep packet inspection (DPI) that looks for encapsulated TCP behaviors or unusual Maximum Transmission Unit (MTU) values. They even leverage browser and device fingerprinting or detect WebRTC leaks that could expose your real IP.
It was a stark reminder that while VPNs are crucial for privacy, there’s an ongoing “arms race” between users and those who seek to monitor or block traffic. This challenge made me wonder: if they can get so clever at detecting, what powerful tools are out there for understanding and testing these network interactions from our own devices, perhaps even something as portable and accessible as our Android? This burning question led me down a fascinating rabbit hole, revealing the incredible potential hidden within our mobile devices. And if you’ve ever felt that frustration, that desire to truly understand what’s happening beneath the surface, then trust me, I’ve been there. And I’ve found some answers I’m excited to share.
Why the “Proxy or Unblocker” Message Still Haunts Your VPN?
It’s a frustrating message, isn’t it? You fire up your trusty VPN, expecting seamless access, and then, bam! – that annoying pop-up appears, or content simply refuses to load. It feels like a digital brick wall, right? Well, it’s not just bad luck, and it’s certainly not your fault. There are very specific, and often powerful, reasons why websites and Internet Service Providers (ISPs) are so keen on spotting and blocking VPN usage. It’s a bit of an “arms race” out there, between those of us seeking privacy, access and free flow of information, and those trying to monitor or restrict it.
First off, let’s talk about those location-based restrictions, because that’s often the most common culprit when you’re trying to unwind with a show. Streaming giants like Netflix and BBC iPlayer operate under strict geographical licensing agreements. This means a show available in one country might be entirely absent in another.
When you use a VPN to “teleport” your IP address to a different country, you’re essentially trying to bypass these rules. For these platforms, it’s not about being mean; it’s about avoiding legal and financial headaches and sticking to their content deals.
For example, Netflix faced pressure from major film studios to block VPN access when people in Australia were already watching it before it was officially available there. And BBC iPlayer, as you might have experienced, is explicitly designed for UK TV Licence holders, and they’ve gotten quite good at detecting when connections come from “abnormal” numbers of simultaneous connections from the same IP address, flagging it as a VPN.
It’s a constant battle, with platforms “constantly updating how they detect and block VPN traffic”.
Beyond entertainment, there’s a more serious layer: complying with government regulations and censorship laws. In many parts of the world – think places like China, Russia, Iran, or Syria – governments outright ban or heavily restrict certain online content and websites. ISPs and digital services in these regions are required to comply with these restrictions. Blocking VPN traffic helps them avoid severe legal and financial penalties, especially since it’s tough to know what kind of content is being accessed through an encrypted tunnel.
And I think some schools, colleges, universities are among those who do care if you are using a VPN or not too. They want to conserve the capacity of bandwidth and make sure the internet service provided by school is used for study purposes.
Countries like China have even instructed telecom carriers to block personal VPN use and their Great Firewall is designed to “learn, discover and block” encrypted VPN communications.
Then there’s the issue of preventing fraud and abuse. Imagine running an online store with different prices for different regions, or a bank trying to monitor suspicious login attempts. When someone uses a VPN, it blurs their true location, which can trip up these fraud prevention systems.
A VPN can make it seem like a single user is accessing hundreds of different IP addresses, which is often a red flag for bot attacks or attempts to bypass rate limits. I once came across a line that said, “in the eyes of fraud prevention systems, VPN usage can be a red flag”. It doesn’t mean you’re doing anything wrong, but your VPN can make your connection look suspicious to their automated systems.
Finally, ISPs are also concerned with network management and throttling. Even though your VPN encrypts your traffic so they can’t see what you’re doing (like the specific movie you’re streaming or file you’re downloading), they can still see how much data you’re transferring. This allows them to make “educated guesses about your activities” – for instance, if you’re using a ton of data, they might suspect streaming or large downloads.
Some ISPs are even legally allowed to slow down your internet speed. So, if they detect VPN traffic, they might throttle it, even if they can’t see the content itself. It’s a way for them to manage network congestion or discourage certain types of high-bandwidth usage that they assume is happening behind the VPN.
So, when you see that “proxy or unblocker” message, it’s usually one of these underlying motivations at play. It’s a testament to the sophisticated – and constantly evolving – methods these entities use to understand and control online traffic. But understanding why they do it is the first step to figuring out how to navigate this complex landscape.
Unmasking the Methods: How ISPs and Websites Spot Your VPN
Alright, let’s pull back the curtain on how those websites and your Internet Service Provider (ISP) manage to figure out you’re using a VPN. It’s not magic, but it involves some pretty clever technical detective work. Think of it like a game of hide-and-seek, but instead of hiding behind a tree, your VPN is trying to hide your entire online presence!
When you connect to a VPN, you’re essentially rerouting your internet traffic through a server run by your VPN provider. This server works like a middleman – it sends your requests to the internet and brings the responses back, keeping your real identity out of the picture. While this process is great for privacy, it also creates certain patterns that can give your VPN away. Here’s how they do it:
The Obvious Trail: Known VPN Server IPs and Datacenter Clues
One of the most straightforward ways for websites and ISPs to detect VPN usage is by looking at the IP address you’re connecting from.
Public VPN IP Blacklists
Imagine a popular VPN service with thousands, or even millions, of users. All these users connect through a relatively limited pool of server IP addresses. If a website sees a single IP address suddenly generating traffic from dozens of different users, or in ways that aren’t typical for a regular home internet connection, that’s a huge red flag. These “unfamiliar IP addresses” are quickly flagged as known VPN IPs and get added to blacklists. This is why you might try to access a streaming service, and it immediately says, “Proxy or Unblocker detected!” They simply know that IP belongs to a VPN.
The VPN Exit Node Enumeration Process
Companies that want to detect VPNs actually go to great lengths to build these blacklists. They might systematically purchase paid subscriptions from major VPN providers like NordVPN or ExpressVPN. Then, they connect to every available server region provided by that VPN and log the IP address they get. This process, called “VPN Exit Node Enumeration,” creates highly accurate lists of VPN server IPs, ensuring that if you’re using one of those, you’re likely to be detected.
Datacenter vs. Residential IPs
Even if you’re tech-savvy and set up your own VPN on a Virtual Private Server (VPS) – basically, a small server you rent online – it might still be detected. Why? Because the IP address provided by most VPS hosts belongs to a datacenter, not a typical residential internet connection. Websites and services know the difference, and traffic from a datacenter IP can be a giveaway that you’re not browsing from a home network. It’s even possible that an IP from a VPS was previously used by someone else for “shady” activities, getting it blacklisted before you even started using it.
Subtle Signals: Protocol Information and Deep Packet Inspection (DPI)
Beyond just the IP address, there are more advanced, technical ways that networks can peer into your connection.
VPN Protocol Information and Specific Ports
Think of VPN protocols like different languages your VPN speaks to connect to its server. Each language, or protocol (like OpenVPN, WireGuard, or IKEv2), often uses very specific “ports” on the internet to communicate. For example, OpenVPN commonly uses port 1194, though it can also use 443 or 80. WireGuard often uses port 51820, and IKEv2 uses 500 or 4500.
Your ISP or a website can monitor traffic on these known VPN-associated ports. If they see a lot of activity on these specific ports, it’s a strong indicator that a VPN is in use.
This method is particularly common in environments with strict network controls, like some corporate networks or government firewalls. However, it’s not foolproof, as some legitimate applications might also use these ports, leading to potential “false alarms”.
Use Wireshark software to examine
Here, the someone means the person who has access to routers in a network. Certainly not an average person can do that.
Someone can install a software called Wireshark on a getaway device in the network to monitor all traffic going through. Since a traditional VPN uses AH and ESP protocols, he/she can easily identify them in Wireshark.
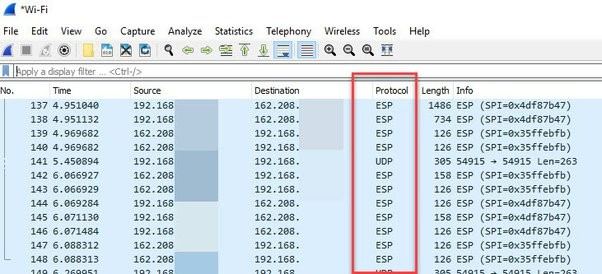
While you use a VPN, in order to avoid DNS leak, VPN configuration would force DNS requests to the DNS server of a VPN provider via the VPN tunnel. With Wireshark, someone can see that traffic on port 443, if he/she see that almost all the traffic from a single IP address is using HTTPS/TCP 443 and there is no any DNS request from the IP address, then he/she can know that you are using a VPN.
Deep Packet Inspection (DPI) and Encapsulated TCP Behavior
This is where it gets really clever. Deep Packet Inspection (DPI) is a technique that lets ISPs and censors examine the actual data packets flowing through their networks, even if they’re encrypted. While they can’t read the content of your encrypted traffic, they can look at its structure and behavior.
A sophisticated technique involves detecting “encapsulated TCP behaviors” within UDP-based VPN connections. This is a “protocol-agnostic” method, meaning it doesn’t care which specific VPN protocol you’re using; it just looks for underlying patterns.
Even when a common internet protocol like TCP (Transmission Control Protocol) is wrapped inside an encrypted UDP (User Datagram Protocol) tunnel by your VPN, it still exhibits “distinct and easily measurable patterns in the size, direction, and timing of packets”. These patterns are based on how TCP is supposed to behave, as defined by internet standards (RFCs).
Researchers have identified key TCP behaviors that can leak, even when tunneled:
- Three-Way Handshake (3WHS): This is the “hello-hello-back-to-you” sequence (SYN, SYN-ACK, ACK) that TCP uses to establish a connection. Even without seeing the actual TCP flags, clever analysis of packet size, direction, and timing within the first 20 packets can reveal this handshake.
- 500msACK: TCP usually sends an acknowledgment (ACK) packet within 500 milliseconds after receiving a data chunk. If a UDP stream consistently shows this timing, it’s a strong hint that TCP traffic is hidden inside.
- 2RMSS: This refers to an ACK packet sent after receiving a specific amount of data – twice the “Maximum Segment Size” (RMSS). This pattern also gives away the presence of tunneled TCP.
This technique is highly accurate, achieving a false positive rate (FPR) as low as 0.11% – meaning it rarely mistakes regular traffic for VPN traffic. This level of accuracy is “an order of magnitude lower than existing machine learning-based VPN detection methods” and is comparable to what real-world censors like China’s Great Firewall use.
Unusual Maximum Transmission Unit (MTU) Values
The Maximum Transmission Unit (MTU) is essentially the largest size a packet of data can be. Different VPN protocols often adjust these MTU values to fit their encryption or network needs. For example, a standard Ethernet connection might have an MTU of 1500, but a VPN might lower it to, say, 1400, to avoid breaking up large packets into smaller ones.
These unusual MTU sizes can be a clue that a VPN is in use, especially if they don’t match what’s expected from typical home internet traffic.
However, this method isn’t perfect, as things like your router settings or even a shaky Wi-Fi connection can also affect MTU values, so it’s usually used as part of a bigger detection strategy.
Digital Footprints: Browser and Device Fingerprinting
Even your own device and browser can inadvertently leak clues about your real identity or location, especially when combined with VPN usage.
Time Zone Inconsistencies
Your web browser often reveals your device’s local time settings. If your VPN says you’re browsing from a server in Berlin, but your device is set to Pacific Time, that’s a “red flag”. Imagine logging in from Los Angeles, and then a few seconds later, appearing to log in from Tokyo – this “impossible travel” scenario is a very strong indicator of VPN use.
Cross-Checking Device Location Against IP Location
Many devices, especially smartphones and newer laptops, can share your GPS or Wi-Fi-based location data with websites. If your VPN says you’re in London, but your phone’s GPS says you’re still in Jakarta, that mismatch can trigger VPN detection systems. Websites can even compare this live location data with your past login patterns.
Browser Fingerprints
Every time you visit a website, your browser leaves behind a unique “fingerprint” of identifiable clues. This includes details like:
- Your operating system (Windows, macOS, Android, etc.).
- Your screen size and resolution.
- Your time zone (again!).
- Your language settings.
- Even the fonts you have installed
When enough of these signals are combined, they create a fingerprint that’s almost as unique as your real one. If your VPN gives you an Italian IP address, but your browser settings consistently show you’re in California with English language settings, that kind of inconsistency can easily flag you for further review.
WebRTC Leaks
This is a particularly nasty one for VPN users. Web Real-Time Communication (WebRTC) is a browser feature that allows direct communication between devices for things like video calls or live streaming, making them faster and smoother. However, to enable this direct communication, WebRTC often needs to know the real public IP addresses of the devices involved.
The problem? Even if you’re using a VPN, WebRTC can sometimes “leak” your real IP address, completely bypassing your VPN’s encryption and revealing your true location. This is a “major problem” because it defeats the whole purpose of using a VPN to hide your IP. Browsers like Firefox, Google Chrome, Opera, and Microsoft Edge are particularly vulnerable to these leaks by default.
While some good VPNs are designed to prevent WebRTC leaks, it’s something you always need to be aware of and check for. Related to this, your real DNS server IP address or even your IPv6 address can sometimes “leak” outside the VPN tunnel, also exposing your real location.
As you can see, the ways websites and ISPs try to unmask VPN users are quite varied and constantly evolving. It’s a complex dance between privacy tools and detection methods, but knowing how they try to spot you is the first step in staying hidden!
Beyond Encryption: What Your VPN Really Hides (and Reveals)
Alright, you’ve got your VPN all set up, and you’re feeling pretty secure, right? That’s great! But it’s super important to understand that while a VPN is a powerful tool for privacy, it’s not an invisibility cloak. There are certain things your Internet Service Provider (ISP) and the websites you visit can still see, even when your VPN is active. Think of it like a highly encrypted package – they might see the package, who sent it (the VPN server), and how big it is, but they can’t open it to see what’s inside.
The core magic of a quality VPN is encryption, which scrambles your online data into an unreadable format. This “secure tunnel” is what primarily protects your actual activities from prying eyes. But let’s break down exactly what stays hidden and what peeks through.
What Your ISP and Websites CAN Still See (The VPN’s “Reveals”)
Even with a VPN, your ISP is still handling all your internet traffic, so they definitely notice certain things about your connection, even if they can’t see the specifics of your activities.
That You’re Connected to a VPN Server
This is the big one, and it’s pretty hard to hide. Your ISP sees your internet traffic going to an unfamiliar IP address – which is the VPN server – instead of directly to the websites you’re trying to reach. It’s a recognizable pattern that shouts, “Hey, this person is using a VPN!”. They know you’re using a privacy tool, but not what you’re doing with it.
The VPN Server’s IP Address
When you’re connected to a VPN, all your online traffic appears to come from a single IP address: the VPN server’s. This is different from normal browsing, where your traffic would go to many different website servers directly.
By looking at this specific IP address and comparing it against known databases of VPN server IPs, your ISP or a website can often identify the specific VPN service you’re using. This doesn’t reveal your activity, but it confirms you’re using a VPN.
These VPN server IPs are often “flagged as known VPN IPs” and added to blacklists. Even if you set up your own VPN on a Virtual Private Server (VPS), its IP might be known to belong to a datacenter and not a typical home internet connection, making it detectable.
The VPN Protocol Being Used
Think of VPN protocols like different languages your VPN speaks to connect to its server. Each “language” (like OpenVPN, WireGuard, or IKEv2) often uses very specific “ports” on the internet to communicate. For example, OpenVPN often uses port 1194, or sometimes 443 or 80. WireGuard commonly uses port 51820. IKEv2 uses ports 500 or 4500.
Your ISP can monitor traffic on these “VPN-associated ports”. If they see a lot of activity on these specific ports, it’s a strong indicator that a VPN is in use. This helps them identify which VPN technology you’re using, but still not the content.
Connection Timestamps and Duration
Your ISP keeps track of when you start and stop using your internet connection, and how long it lasts. This is true for all your internet usage, and it’s no different when you’re using a VPN. So, they’ll know exactly when you connected to your VPN and for how long you stayed connected. They know your general usage patterns, but they can’t link them to specific online actions.
Bandwidth Usage Patterns
Your ISP can see the amount of data you’re transferring. While they can’t see what you’re downloading or streaming, they can make educated guesses. For instance, if you’re using a lot of data, they might suspect you’re streaming movies or downloading large files, because these activities typically consume more bandwidth than just browsing. However, they still cannot see the actual content or sources.
What a Quality VPN CAN Hide (The VPN’s “Shield”)
Now for the good news! This is where your VPN truly shines and protects your privacy. A good VPN works by encrypting your internet traffic, creating a secure tunnel that essentially blinds your ISP and most websites to your actual online activities.
- Websites You Visit and Your Browsing History This is a big one for privacy. Your ISP cannot see which specific websites you visit, your detailed browsing history, the URLs of pages you open, or the content on those pages. This is crucial because it prevents ISPs from building detailed profiles about your interests and habits, which could otherwise be used for targeted advertising or government surveillance.
- Your Search Queries When you search for something online, those search terms and even the search engines you use remain encrypted and invisible to your ISP. This means your private research, personal interests, or any sensitive topics you look up stay completely confidential.
- Files You Download or Upload Whether you’re downloading documents, software, or uploading photos, your ISP cannot see the specific files, their content, their types, or their sources. This is especially important for preventing ISPs from slowing down your connection (throttling) based on file-sharing activities or reporting your download behavior.
- Streaming Activity Enjoying Netflix, Hulu, or BBC iPlayer? Your ISP cannot see which streaming services you use, what specific content you’re watching, or even the quality of your streaming. This helps to avoid bandwidth throttling during peak streaming hours and prevents ISPs from blocking or prioritizing certain streaming services based on your activity. Although, be aware that some streaming services actively try to block VPNs to enforce geo-restrictions.
- Personal Information You Enter Online Any sensitive data you input on websites, such as login credentials, credit card details, or other financial information, is encrypted by your VPN. This protects your sensitive information from ISP monitoring and reduces the data available in potential security breaches.
- Messaging Content Your private communications, including the content of your emails and their recipients, your activity on messaging apps and social media, and even who you’re talking to in video calls, remain private and encrypted. This ensures confidentiality and prevents ISPs from selling your communication data to third parties.
- Your Real IP Address The fundamental purpose of a VPN is to mask your true IP address. When your VPN is working correctly, your real IP address is hidden, and websites only see the IP address of the VPN server you’re connected to. However, be mindful of WebRTC leaks, which are a “major problem” where a browser feature can sometimes reveal your real public IP address even with a VPN active, defeating the purpose of hiding your IP. Good VPNs should prevent these leaks.
Here’s a quick table to summarize what your ISP can and cannot see:
| What Your ISP & Websites CAN See | What Quality VPNs HIDE |
| ✅ That you’re connected to a VPN server | ❌ Websites you visit |
| ✅ The VPN server’s IP address | ❌ Your search queries |
| ✅ VPN protocol being used (e.g., OpenVPN, WireGuard) | ❌ Files you download or upload |
| ✅ When you connect and disconnect | ❌ Personal information you enter |
| ✅ Amount of data transferred (bandwidth usage) | ❌ Your actual browsing history |
| ❌ Specific streaming content | |
| ❌ Email and messaging content | |
| ❌ Your real IP address (if no leaks) |
So, while your ISP and websites can tell you’re using a VPN, they’re mostly in the dark about what you’re actually doing online. This makes a quality VPN an essential tool for maintaining your digital privacy in today’s world.
Outsmarting the Blocks: Advanced Strategies for VPN Evasion
We’ve talked about what your VPN can and can’t hide, and it’s clear that while it’s a fantastic privacy tool, it’s not totally invisible. Think of it like a game of hide-and-seek online – your VPN is trying its best to keep you hidden, but the “seekers” (ISPs, websites, governments) are getting really good at spotting the signs of a VPN connection.
But don’t worry! This doesn’t mean your privacy efforts are useless. It just means you need to be smart about how you use your VPN and choose a good one that plays the game even better. This is where advanced strategies for VPN evasion come in – techniques employed by both VPN providers and you, the user, to stay ahead in this online “arms race”.
It’s a constant back-and-forth, with detection methods getting more sophisticated and VPNs evolving to counter them. Let’s look at the cool tricks that help your VPN fly under the radar and what you can do to boost your privacy even further.
How VPN Providers Help You Stay Hidden (and How You Benefit)
Your VPN provider isn’t just giving you an encrypted tunnel; they’re constantly developing new ways to make that tunnel look like normal internet traffic, so it’s harder to spot.
Obfuscated Servers or Stealth Protocols
The Art of Disguise Imagine trying to sneak into a party disguised as a waiter. That’s what obfuscated servers or stealth protocols do for your VPN traffic. They’re designed to “disguise VPN traffic” and make it appear as regular internet traffic, rather than the distinct patterns of a VPN.
This is super important in “restricted regions” where governments actively block VPNs, like China or Iran. Some VPNs, like NordVPN and ExpressVPN, offer this as a built-in feature. For instance, after China started using deep packet inspection (a way of looking deeply into data packets), a firm called Golden Frog began “scrambling OpenVPN packet metadata” to avoid detection. This helps bypass those strict firewalls and censorship.
Rotating IP Addresses: Always on the Move
One of the easiest ways for websites and ISPs to detect a VPN is by keeping a “blacklist” of known VPN server IP addresses. If your VPN server’s IP address is on that list, you’re immediately flagged. To combat this, quality VPN providers constantly “rotate their server IP addresses”, meaning they frequently change the public-facing IP addresses of their servers. It’s like changing your hide-and-seek spot every few minutes – it makes it much harder for the “seeker” to keep up.
Using Non-Default or Common Ports: Blending In
Just like different VPN protocols have specific “languages” (or ports) they usually use for communication (e.g., OpenVPN often uses 1194 or 443, WireGuard uses 51820), these can be monitored by your ISP.
A smart strategy is for VPNs to use “non-default ports” or, even better, “common ports like 443 (HTTPS)”. Port 443 is what regular, secure website traffic (like when you visit your bank or a shopping site) uses. If your VPN traffic also uses this port, it becomes much harder for an ISP to distinguish it from everyday web browsing. It’s like hiding in plain sight!
Random Padding and Timing Obfuscation: Adding Noise to the Signal
Imagine you’re trying to figure out what’s inside a box by just feeling its weight and size. If someone added random packing peanuts inside, it would be harder to guess, right?
- “Random padding” means adding extra, meaningless data to your encrypted packets, changing their sizes and making them less predictable.
- “Timing obfuscation” involves artificially inserting tiny, random delays between packets.
Both these techniques are designed to “increase the difficulty of traffic metadata attacks”, which rely on analyzing patterns in packet sizes and timings to identify VPN usage. While research suggests random padding only “slightly increases the difficulty”, it still helps.
Connection Multiplexing: The Crowd Effect
This is a powerful technique where VPNs route “multiple TCP streams and other traffic (like DNS)” through a single VPN tunnel.
Think of it like trying to pick out one person’s conversation in a very crowded room. When all your different online activities (browsing, streaming, chatting) are mixed together and sent through one VPN tunnel, it becomes incredibly difficult for an ISP or censor to analyze individual connections and identify VPN patterns. This method “shows more promise to be a robust defense” against detection.
Dedicated IP Addresses: Your Own Secret Entrance
Most commercial VPNs share IP addresses among many users, which can lead to those IPs being flagged and blacklisted. Some VPN services offer “dedicated personal proxy IPs”, like Surfshark.
This means you get an IP address that only you use. It’s less likely to be flagged as a generic VPN server IP because it behaves more like a regular residential IP address, making detection harder. However, as with any trade-off, having a dedicated IP might offer slightly less anonymity than a shared one, because your activity isn’t mixed with others’.
Essential VPN Features for Your Digital Shield
Beyond what VPN providers do in the background, there are crucial features you should always enable and look for in a VPN to protect yourself.
- DNS Leak Protection: Guarding Your Online Address Book Your computer uses a “DNS” (Domain Name System) server to translate website names (like “google.com”) into IP addresses (like “172.217.160.142”). A DNS leak happens when these requests go outside your encrypted VPN tunnel to your ISP’s DNS servers instead of the VPN’s, potentially revealing the websites you’re visiting and even your real IP address.
- A good VPN will have “DNS leak protection” built-in, ensuring all your DNS queries stay within the secure VPN tunnel. You can even check for this yourself using tools like Hide.me’s “DNS Leak Test”.
- Kill Switch: Your Last Line of Defense What happens if your VPN connection suddenly drops? Without a kill switch, your device would immediately revert to your regular, unprotected internet connection, exposing your real IP address and online activities to your ISP.
- A kill switch is a critical security feature that automatically “disconnects your internet if the VPN connection drops”. This prevents any accidental data leaks, ensuring your online activities remain private, even if the VPN temporarily fails. Always make sure this feature is enabled!
Your Personal Best Practices for Uninterrupted Privacy
Even with the best VPN, your own habits can play a big role in whether you get detected. These simple steps can make a huge difference.
- Clear Your Cookies and Cache: Erasing Your Digital Footprints Websites, especially streaming services, often use cookies and cache to remember information about your past visits, including your real geographic location. If you connect to a VPN server in a different country but your browser still has old location data stored, the website might detect a mismatch and block you.
“Clearing cookies/cache” after switching VPN servers helps reset this, making it appear as if you’re a brand new visitor from your chosen VPN location. It’s a simple trick, but highly effective for bypassing geo-restrictions.
- Disable GPS or Browser-Based Location: Don’t Give Yourself Away Many modern devices, particularly phones and laptops, can share your “GPS or Wi-Fi-based location data” with websites. If your VPN says you’re in London, but your device’s GPS says you’re in Jakarta, that’s a dead giveaway that you’re using a VPN.
To prevent this, it’s wise to “explicitly turn off location services” on your device or in your browser settings when using a VPN. This prevents those sneaky location mismatches from being used to detect your VPN.
Choose Quality, Reputable VPN Providers (and Avoid Free Ones!): Your Foundation of Trust
This is perhaps the most important advice I could give you since not all VPNs are created equal.
- Quality VPNs invest in robust security. Look for providers with a “no-logs policy verified by independent audits”, meaning they don’t keep records of your online activities. They should offer “strong encryption (AES-256 or equivalent)”, which is like having an unbreakable lock on your data. Features like a kill switch and DNS leak protection are non-negotiable.
- “Free VPNs are generally not recommended” because they come with significant privacy and security risks. Many free VPNs “often sell user data to advertisers,” use “weak encryption,” may contain “malware risks,” and offer “poor performance” due to “limited servers”. You might think you’re getting something for free, but you could be paying with your privacy. Paid VPN services, like ExpressVPN, invest in proper security and don’t sell user data.
Here’s a quick summary of these advanced evasion strategies:
| Evasion Strategy | Who Uses It | How It Helps |
|---|---|---|
| Obfuscated Servers | VPN Provider | Disguises VPN traffic to look like regular HTTPS, bypassing strict firewalls. |
| Rotating IP Addresses | VPN Provider | Constantly changes server IPs to avoid blacklists of known VPN addresses. |
| Non-Default/Common Ports | VPN Provider | Routes VPN traffic through less common ports or standard ones (like 443) to blend in. |
| Random Padding/Timing Obfuscation | VPN Provider | Adds random data/delays to packets, making traffic analysis harder. |
| Connection Multiplexing | VPN Provider | Mixes various types of traffic within one tunnel, obscuring individual activities. |
| Dedicated IP Addresses | VPN Provider (Paid) | Provides a unique IP that’s less likely to be flagged as a shared VPN server. |
| DNS Leak Protection | VPN Feature | Ensures all DNS requests go through the VPN, hiding visited sites from your ISP. |
| Kill Switch | VPN Feature | Automatically cuts your internet if the VPN drops, preventing accidental exposure. |
| Clear Cookies/Cache | User Action | Removes old location data from your browser, helping bypass geo-blocks. |
| Disable Location Services | User Action | Prevents devices from sharing real GPS/Wi-Fi location that contradicts VPN’s IP. |
| Choose Quality VPNs | User Choice | Ensures strong encryption, no-logs policy, and advanced features for robust privacy. |
Once you get the hang of these strategies and actually start using them, your VPN game gets a whole lot stronger. You’ll be able to keep your privacy tighter and access more of the web without hitting as many walls. Yeah, it’s kind of a constant cat-and-mouse thing – but with the right tools and a bit of know-how, you can definitely stay ahead of the game.
From User to Expert: Demystifying Network Interactions with Your Device
Alright, we’ve talked a lot about how big companies, ISPs, and even governments can spot VPN usage, and why they might want to. We’ve seen that it’s a constant “arms race” between those trying to detect VPNs and VPN providers trying to stay hidden. But what does all this mean for you and your devices? How can you become a bit of a “network detective” and truly understand what information your phone or computer is sending out into the digital world, even if you don’t have a background in IT?
This section is all about empowering you. It’s about taking those complex detection methods we’ve discussed and turning them into actionable insights for your own digital privacy and security journey. While we won’t be diving into specific, advanced tools like Kali NetHunter(I have made a video of it, you can watch it here). We will explore the fundamental principles that govern how your device interacts with the internet and what clues it might leave behind. Understanding these “clues” is the first step to better protecting your online presence.
What Your Device Inevitably Broadcasts (Even with a VPN On)
Think of your internet connection like sending a letter. A VPN is like sending that letter through a special, encrypted post office (the VPN server) before it goes to its final destination. While the contents of your letter (your browsing data, search queries, downloads) are sealed away and unreadable to your ISP, some basic information about the “envelope” and its journey is still visible.
Here’s what your Internet Service Provider (ISP) – the company that gives you internet access – can always see, even when you’re using a top-notch VPN:
- Your VPN Connection Status: Your ISP will definitely know that you’re connected to something that isn’t a regular website. Instead of seeing your device talking directly to Google or Netflix, they see it talking to a VPN server’s IP address. This is like them seeing you always sending your letters to that one special post office, instead of directly to all your different friends.
- The VPN Server’s IP Address: Since all your traffic is routed through the VPN server, your ISP will see that specific IP address. Many VPN providers use pools of these IP addresses, and over time, these IPs become known and can be “flagged as known VPN IPs” and added to blacklists by detection systems. Even if you set up your own private VPN on a Virtual Private Server (VPS), its IP might be flagged because it’s known to belong to a datacenter, not a typical home internet connection.
- The VPN Protocol Being Used: Believe it or not, different VPN “languages” or protocols (like OpenVPN or WireGuard) often use specific “doorways” or network ports. Your ISP can observe traffic flowing through these specific ports, giving them a clue about the underlying VPN technology you’re using.
- Connection Timestamps and Duration: Just like with any regular internet usage, your ISP can see when you start and stop your VPN connection and how long you stay connected. This doesn’t reveal what you’re doing, but it gives them a general idea of your online habits.
- Amount of Data Transferred (Bandwidth Usage Patterns): Your ISP can monitor the volume of data you’re sending and receiving. While they can’t see the specific content (e.g., which show you’re streaming), they might make educated guesses about your activities if you’re using a lot of data (e.g., “they’re probably streaming or downloading large files”).
So, while your privacy is significantly enhanced with a quality VPN, it’s important to understand that your online activity isn’t completely invisible to your ISP. They know you’re using a VPN, and they can see some basic details about that connection.
Unmasking the “Hidden” Leaks: Becoming a Network Detective for Your Own Device
Beyond what your ISP sees, your device itself might unintentionally reveal information, especially if your VPN isn’t configured perfectly or if you’re not aware of certain browser features. These are often called “leaks,” and understanding them is where you start to become your own network expert.
Let’s look at some common “hidden” signals and how you can check them on your own devices:
WebRTC Leakage
Imagine a special kind of phone line on your computer that lets real-time apps like video calls talk directly to another computer. It’s designed to be super fast and efficient!
The Problem: This fast, direct connection often requires that your actual, real IP address be exposed. If your VPN isn’t specifically set up to handle this, your real IP can leak out, completely defeating the purpose of using the VPN to hide your location. It’s like using a secret identity, but your “phone line” still broadcasts your real home address!
How to Check/Mitigate: You can easily test for this by visiting sites like ipleak.net or ExpressVPN’s WebRTC leak test tool. If your real IP shows up, your VPN isn’t protecting you from this specific leak. To fix it, ensure your VPN has a dedicated WebRTC leak protection feature, or, as a last resort, disable WebRTC in your browser settings (though this might affect some real-time apps).
DNS & IPv6 Leaks
Think of the Internet as a massive phone book, and DNS (Domain Name System) is what translates website names (like “google.com”) into numerical IP addresses (like “172.217.160.142”) that computers understand. IPv6 is simply the newer, bigger version of internet addresses.
The Problem: When you use a VPN, your DNS requests should go through the VPN’s “secure tunnel”. If they don’t, your computer might send these requests directly to your ISP’s DNS servers, which can then see what websites you’re trying to visit and even potentially link it back to your real IP address. Similarly, if your VPN only handles IPv4 traffic, your computer might still use its real IPv6 address, revealing your actual location.
How to Check/Mitigate: Use online tools like dnsleak.com or dnsleaktest.com to check for DNS leaks. For IPv6, try ip6.me. If these tests show your real ISP’s DNS server or your real IPv6 address, your VPN isn’t fully protecting you. A quality VPN should offer DNS leak protection. You might also need to configure your VPN to tunnel IPv6 or disable IPv6 on your device if it’s a persistent issue.
Browser Fingerprinting & Location Mismatches
Your web browser, like a unique set of fingerprints, leaves behind many clues about your device and preferences. This includes your operating system (Windows, macOS, Android), screen size, time zone, language settings, and even the fonts you have installed. Many devices, especially phones, can also share GPS or Wi-Fi-based location data.
The Problem: If your browser’s “fingerprint” (e.g., set to Pacific Time, US English) doesn’t match the location your VPN is claiming (e.g., a Berlin IP), this inconsistency can be a huge red flag for websites. Imagine logging in from Los Angeles and then, seconds later, appearing in Tokyo – this “impossible travel” immediately signals something unusual, like VPN use. These subtle mismatches build a “risk profile” about you.
How to Check/Mitigate: While there aren’t simple “tests” for your overall browser fingerprint, being aware of these settings helps. Always ensure your browser’s time zone and language settings match your chosen VPN location. Clear your browser’s cookies and cache regularly, especially after switching VPN servers, as websites might remember your previous (real) location. For mobile devices, explicitly disable GPS or browser-based location services when using a VPN to prevent mismatches.
Unusual Traffic Patterns & Protocol Signatures
This gets a bit more technical, but it’s about the “shape” and “flow” of your data packets. Sometimes, the way a VPN “wraps” your internet traffic (a process called encapsulation) can leave tell-tale signs, like specific Maximum Transmission Unit (MTU) values or distinct TCP behaviors.
The Problem: Even though the content of your data is encrypted, the way it’s packaged can be unique to certain VPN protocols. For example, a research paper highlights how subtle TCP behaviors (like “three-way handshakes” or acknowledgment packet timings) can inadvertently leak the presence of a VPN tunnel, even within encrypted UDP connections. This means sophisticated detection systems can analyze these patterns to infer VPN usage.
How to Check/Mitigate: These are very technical aspects that you, as a user, cannot easily test or control directly. This is where the quality of your VPN provider becomes crucial. Look for VPNs that offer “obfuscated servers” or “stealth protocols”. These features are designed to scramble the packet metadata or make VPN traffic look like regular HTTPS traffic, hiding these distinct patterns. Connection multiplexing (mixing different types of traffic within the VPN tunnel) can also make detection harder.
Empowering Yourself: Moving Beyond Basic VPN Usage
Becoming aware of these potential leaks and digital fingerprints is a powerful step in taking control of your online privacy. It moves you from simply “using a VPN” to actively understanding “how my device interacts with the network.”
Here are some key takeaways to empower you on your digital privacy journey:
- Be Proactive with Leak Tests: Regularly use the suggested online tools (like ipleak.net, dnsleak.com, and ip6.me) to test your VPN connection. These tests are simple to run and can quickly alert you to issues that might compromise your privacy.
- Choose a Quality VPN: This is paramount. Reputable, paid VPN providers invest in features like robust encryption (e.g., AES-256), independently audited no-logs policies, a kill switch (to prevent data leaks if your VPN disconnects), DNS leak protection, and obfuscated servers. Free VPNs, as our sources strongly caution, often lack these essential protections and can even sell your data.
- Configure Your Device and Browser Thoughtfully: Small changes can make a big difference. Get into the habit of clearing your browser’s cookies and cache (especially after switching VPN servers on streaming sites). Consider disabling GPS or browser-based location services on your device when you’re using a VPN to avoid location mismatches.
- Stay Updated: Keep your VPN software and operating system up-to-date. Updates often include crucial security patches and improvements to evasion techniques.
While the we don’t delve into the specifics of advanced tools like Kali NetHunter, the core of what those tools achieve is understanding and analyzing network interactions – exactly what we’ve demystified here. By grasping how your device broadcasts information and how detection systems analyze it, you’re not just a VPN user anymore; you’re an informed participant in your own digital security. This proactive approach ensures that your efforts to protect your privacy are truly effective in the face of evolving detection methods.